Majority of us now use smartphones and we do store our personal as well as some confidential data in it. A lost or stolen phone can be really painful if the owner had any confidential data stored in it. All you need in such situation is a way to delete all those files so that no one can misuse the information on the phone.
Here the F-Secure anti theft system comes in the picture. It is a free mobile software developed by one of the leading company in the field of digital security.
skip to main |
skip to sidebar
.jpg)




 As the fraudsters are now becoming more sophisticated in bypassing the Geo-location controls by using proxies (Anonymous IPs) to spoof their IP address, it has become very much necessary to come up with a means for detecting the proxies so that the authenticity of the users can be verified. Using a proxy (web proxy) is the simplest and easiest way to conceal the IP address of an Internet user and maintain the online privacy. However proxies are more widely used by online fraudsters to engage in cyber crimes since it is the easiest way to hide their actual Geo-location such as city/country through a spoofed IP address. Following are some of the examples where fraudsters use the proxies to hide their actual IP.
As the fraudsters are now becoming more sophisticated in bypassing the Geo-location controls by using proxies (Anonymous IPs) to spoof their IP address, it has become very much necessary to come up with a means for detecting the proxies so that the authenticity of the users can be verified. Using a proxy (web proxy) is the simplest and easiest way to conceal the IP address of an Internet user and maintain the online privacy. However proxies are more widely used by online fraudsters to engage in cyber crimes since it is the easiest way to hide their actual Geo-location such as city/country through a spoofed IP address. Following are some of the examples where fraudsters use the proxies to hide their actual IP.



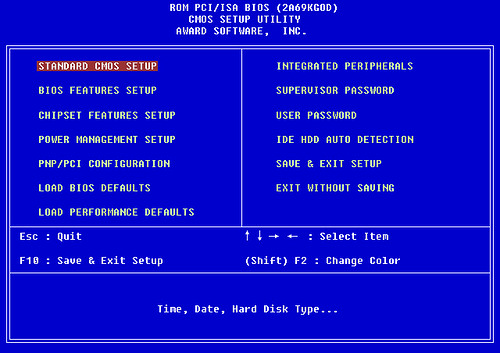 This is a password hack but it clears the BIOS such that the next time you start the PC, the CMOS does not ask for any password. Now if you are able to bring the DOS prompt up, then you will be able to change the BIOS setting to the default. To clear the CMOS do the following:
This is a password hack but it clears the BIOS such that the next time you start the PC, the CMOS does not ask for any password. Now if you are able to bring the DOS prompt up, then you will be able to change the BIOS setting to the default. To clear the CMOS do the following:
Get DOS prompt and type:
 Firefox is the top most world widely used web browser. Because it is handy and have lots of features though its add-on and extension. Sometimes we download files using Firefox and on the same time we need to go for some work. So until we come back the computer waste the energy. In this situation we can use Firefox Auto shutdown thecomputer when downloads are completed and helps us to save electric power.
Firefox is the top most world widely used web browser. Because it is handy and have lots of features though its add-on and extension. Sometimes we download files using Firefox and on the same time we need to go for some work. So until we come back the computer waste the energy. In this situation we can use Firefox Auto shutdown thecomputer when downloads are completed and helps us to save electric power.
 shortening is a trend of the present, but also it’s important for tiny conversations like twitter or facebook status.
shortening is a trend of the present, but also it’s important for tiny conversations like twitter or facebook status.
 Phishing is usually considered to be most effective when it’s combined with social engineering, the hacker term for human manipulation. One way phishing can be combined with social engineering is through the exploitation of redirect vulnerabilities. This article will demonstrate to you what redirect vulnerabilities are, how to spot them, and how they can be exploited.
Phishing is usually considered to be most effective when it’s combined with social engineering, the hacker term for human manipulation. One way phishing can be combined with social engineering is through the exploitation of redirect vulnerabilities. This article will demonstrate to you what redirect vulnerabilities are, how to spot them, and how they can be exploited.
wαит тσ wяiтє likє тнiร??????????......in orkut
a very common javascript
wαит тσ wяiтє likє тнiร??????????......SIMPLE

NOKIA
Nokia Universal Codes
Code Description :
These Nokia codes will work on most Nokia Mobile Phones
Hello Guys I am Going To Explain The Tutorial On Hacking By Using Telnet Service Of Windows Hacking.
NOTE: Will only work if the person you are trying to hack is using a Windows Xp operating system.You need to know victims computers username and password.
Have to be instant messaging victim
WELCOME TO THE HACKER's WORLD. HERE YOU WILL GET HACKING TIPS & TRICKS,LEARN HOW TO HACK, FREE SOFTWARE, MOVIES,HACKING E-BOOKS,PC GAMES & COMPUTER TIPS & TRICKS, ORKUT HACKING, FACEBOOK HACKING, PASSWORD HACKING, HACKING TOOLS, WINDOWS TIPS & TRICKS, BOMB TUTORIALS, WEBSITE HACKING & MUCH MORE ABOUT HACKING.
JOIN US
SEND SMS FROM YOUR MOBILE-
START HACK_ROOM TO 9223050606
ON HACKERS_ROOM TO 9870807070
&
ON HACKERS_ROOM TO 9870807070
Get Free SMS Alert
MY OTHER BLOG
Followers
STEALTH HACKER
.jpg)
Facebook Badge
About Me

- STEALTH_HACKER
- Am a 18 years guy doing CEH & CHFI. I Like To Share My Ideas & Views About HACKING Because i Think That Everyone Should Know About It So That They Can Save Them Self From CRACKERS. "NO ONE CAN SAY AM A HACKER, WE ARE THE HACKERS" HACKING IS NOT CRIME IT's OWN PASSION. BUT ONE CAN USE OF IT FOR GOOD PURPOSE ALSO.
FEEDJIT
Start multiple applications with single click : Lacuna Launcher
Each time after turning on the PC people generally open the same set of applications. For example after turning on my PC I normally open my Firefox browser, Yahoo Messenger and Google Talk and play my same old playlist on Winamp.Time required to open all this programs can be reduced by using this small app – Lacuna Launcher.
Add more options to right click in Windows Explorer
FileMenu Tools allows you to customise the context menu of Windows Explorer. And it lets you:
- Add some built-in utilities that perform operations on files and folders.
Hiren’s BootCD: What is it??
Hiren’s BootCD is an ultimate solution to almost all your computer problems. It comes loaded with hell lot of tools. Each of them is powerful and can be really very helpful if used with caution. You can solve nearly all your PC problems like virus infection, hdd failure, data recovery, Hard disk partitioning, password recovery using this CD.
How to use Cheat Engine for speedhack in CS 1.6
Before you read the following article, see this warning quoted from the developer’s site.
Read before download: Cheat engine is for educational purposes only. Before you attach Cheat Engine to a process, please make sure that you are not violating the EULA/TOS of the specific game/application. cheatengine.org does not condone the illegal use of Cheat Engine
How to show a banner at each startup in Windows

There is a hidden feature in Windows and not many users know anything about it. You can setup a banner with a message in it. Each time your Windows boots up the same banner will pop up. The message can be anything from a welcome message to some important information. You can use it in the way you want. Follow the simple steps given below to setup a banner for your Windows system:
How To Hide Files In A Calculator?
Having read the title of this post you may be wondering if it’s really possible. Yeah! It is possible. As the word suggests, it’s a calculator with a safe which is capable of storing and keeping your files and folders safe. The safe calculator looks just like the default calculator in Windows and in fact it can even perform calculations just like any other calculator. When you start Safe Calculator it will look just like the below pic.
How to Completely Erase a Hard Disk Drive?
A new year has begun and perhaps you have decided to perform a system upgrade or get rid of your old computer system and purchase a new one. But before you sell or donate your old computer, it is very much necessary to completely erase your Hard Disk Drive. Yes, every one of us are aware of this fact and so, we delete the contents of the hard disk either by using the DELETE key on our keyboard or by Formatting the hard disk.
Display Legal Notice on Startup of your Windows

If your PC has multiple users then you can now display legal notice to every user before they login to your PC. This legal notice will be displayed at every startup just before the Desktop is loaded. Using this you can tell your friends about the do’s and dont’s in your computer when they login in your absence. Well you can do this pretty easily. For this there is one small registry hack. Here is the step-by-step instruction to do this.
1. Go to Start->Run, type regedit and hit ENTER
2. Navigate to the following key in the registry
What are Private and Public IP Addresses??

Internet Protocol (IP) addresses are usually of two types:Public and Private. If you have ever wondered to know what is the difference between a public and a private IP address, then you are at the right place. In this post I will try to explain the difference between a public and a private IP addres in layman’s terms so that it becomes simple and easy to understand.
How to Detect Anonymous IP Addresses
 As the fraudsters are now becoming more sophisticated in bypassing the Geo-location controls by using proxies (Anonymous IPs) to spoof their IP address, it has become very much necessary to come up with a means for detecting the proxies so that the authenticity of the users can be verified. Using a proxy (web proxy) is the simplest and easiest way to conceal the IP address of an Internet user and maintain the online privacy. However proxies are more widely used by online fraudsters to engage in cyber crimes since it is the easiest way to hide their actual Geo-location such as city/country through a spoofed IP address. Following are some of the examples where fraudsters use the proxies to hide their actual IP.
As the fraudsters are now becoming more sophisticated in bypassing the Geo-location controls by using proxies (Anonymous IPs) to spoof their IP address, it has become very much necessary to come up with a means for detecting the proxies so that the authenticity of the users can be verified. Using a proxy (web proxy) is the simplest and easiest way to conceal the IP address of an Internet user and maintain the online privacy. However proxies are more widely used by online fraudsters to engage in cyber crimes since it is the easiest way to hide their actual Geo-location such as city/country through a spoofed IP address. Following are some of the examples where fraudsters use the proxies to hide their actual IP.Netbios Hacking- The Ethical Hacking

THIS NETBIOS HACKING GUIDE WILL TELL YOU ABOUT HACKING REMOTE COMPUTER AND GAINING ACCESS TO IT’S HARD-DISK OR PRINTER.NETBIOS HACK IS THE EASIEST WAY TO BREAK INTO A REMOTE COMPUTER.
What are IP Addresses??
An IP address (Internet Protocol address) is a unique address that certain electronic devices currently use in order to identify and communicate with each other on a computer network utilizing the Internet Protocol standard (IP)—in simpler terms, a computer address.
Shutdown your PC remotely using Twitter and TweetMyPC

Twitter is powerful and simple indeed. But then developers were not stopping on creating and obviously developing new applications to make it even stronger. TweetMyPC is a freeware application which enables you to utilize Twitteras a way of sending commands to your PC remotely.
Learn Hacking Step by Step – Understanding the Dangers Your Systems Face
It’s one thing to know that your systems generally are under fire from hackers around the world. It’s another to understand specific attacks against your systems that are possible.
Many information-security vulnerabilities aren’t critical by themselves.
However, exploiting several vulnerabilities at the same time can take its toll.
However, exploiting several vulnerabilities at the same time can take its toll.
A Port Scanner in VB

A small but effective tool (if you know the right way to use it..you might do wonders..)
——————–
you need:
you need:
2 textboxes
1 listbox
3 commandbuttons
1 timer
1 winsock control
——————–
1 listbox
3 commandbuttons
1 timer
1 winsock control
——————–
Basic BIOS password crack
 This is a password hack but it clears the BIOS such that the next time you start the PC, the CMOS does not ask for any password. Now if you are able to bring the DOS prompt up, then you will be able to change the BIOS setting to the default. To clear the CMOS do the following:
This is a password hack but it clears the BIOS such that the next time you start the PC, the CMOS does not ask for any password. Now if you are able to bring the DOS prompt up, then you will be able to change the BIOS setting to the default. To clear the CMOS do the following:Get DOS prompt and type:
CRACK WIFI – Simple WEP Crack
Overview
To crack the WEP key for an access point, we need to gather lots of initialization vectors (IVs). Normal network traffic does not typically generate these IVs very quickly. Theoretically, if you are patient, you can gather sufficient IVs to crack the WEP key by simply listening to the network traffic and saving them. Since none of us are patient, we use a technique called injection to speed up the process . Injection involves having the access point(AP) resend selected packetsover and over very rapidly. This allows us to capture a large number of IVs in a short period of time.
How to Shutdown Computer automatically Using Firefox Auto Shutdown Add-on
 Firefox is the top most world widely used web browser. Because it is handy and have lots of features though its add-on and extension. Sometimes we download files using Firefox and on the same time we need to go for some work. So until we come back the computer waste the energy. In this situation we can use Firefox Auto shutdown thecomputer when downloads are completed and helps us to save electric power.
Firefox is the top most world widely used web browser. Because it is handy and have lots of features though its add-on and extension. Sometimes we download files using Firefox and on the same time we need to go for some work. So until we come back the computer waste the energy. In this situation we can use Firefox Auto shutdown thecomputer when downloads are completed and helps us to save electric power.Windows 7 God Mode
Windows 7 is predominantly the best OS ever in the history of Microsoft. But, do you know that it has a GodMode within it ?
There is a hidden “GodMode” feature that lets a user access all of the operating system’s control panel features from within a single folder.
There is a hidden “GodMode” feature that lets a user access all of the operating system’s control panel features from within a single folder.
How do I Check the Real Link of a Shortened URL?
URL Shortening is a trend in today’s social media and web surfing. Big giants such as Google and YouTube have their own URL shorteners, too. It’s not just because the URL
 shortening is a trend of the present, but also it’s important for tiny conversations like twitter or facebook status.
shortening is a trend of the present, but also it’s important for tiny conversations like twitter or facebook status.
The trend, URL Shortening, was founded by Tinyurl.com at first and spread widely by twitter. Because you’re limited by how many characters you can use in your conversation, you need everything Short but right. That’s why URL Shortening is important and popular at the same time.
Tinyurl.com has an option to preview the shortened link before you visit the site. If you include a word, preview, before the domain tinyurl.com, you will see where the link goes. But what about other shorteners?
Well, you can easily check the link before you have a go to any shortened URL by this firefox plugin. But sometimes you just don’t want to restart your firefox and want a quicker way to do this.
Exploiting Redirect Vulnerabilities
 Phishing is usually considered to be most effective when it’s combined with social engineering, the hacker term for human manipulation. One way phishing can be combined with social engineering is through the exploitation of redirect vulnerabilities. This article will demonstrate to you what redirect vulnerabilities are, how to spot them, and how they can be exploited.
Phishing is usually considered to be most effective when it’s combined with social engineering, the hacker term for human manipulation. One way phishing can be combined with social engineering is through the exploitation of redirect vulnerabilities. This article will demonstrate to you what redirect vulnerabilities are, how to spot them, and how they can be exploited.
So first things first. What is aredirect vulnerability? A redirectvulnerability is when a webpage uses a script toredirect you to somewhere (usually another page on the website), but they write that script in such a way that it allows a hacker to manipulate it to send you to an external page instead of an internal one. There are many types of redirect vulnerabilities, but we’ll be looking at the most basic type here for now. Example: let’s say we’re logging in to webpage that has this url:
10 Tips to Secure Your Twitter Account
Twitter much like Facebook is popular social networking site and these sites users are targeted with phishing scams luring them to reveal their username and passwords.Here are some security tips for twitter users for safe tweeting.
Tips to secure twitter account..
1.Use strong and Unique password : Use the password for your twitter account as a combination of characters, symbols and numbers. Never use same password for different websites and email accounts, use unique password for every website.
wαит тσ wяiтє likє тнiร??????????.....
wαит тσ wяiтє likє тнiร??????????......in orkut
a very common javascript
wαит тσ wяiтє likє тнiร??????????......SIMPLE
Top Movies on Computer Hackings
1) Sneakers (1992)

Martin Bishop is the head of a group of experts who specialise in testing security systems. When he is blackmailed by Government agents into stealing a top secret black box, the team find themselves embroiled in a game of danger and intrigue. After they recover the box, they discover that it has the capability to decode all existing encryption systems around the world, and that the agents who hired them didn’t work for the Government after all…

Martin Bishop is the head of a group of experts who specialise in testing security systems. When he is blackmailed by Government agents into stealing a top secret black box, the team find themselves embroiled in a game of danger and intrigue. After they recover the box, they discover that it has the capability to decode all existing encryption systems around the world, and that the agents who hired them didn’t work for the Government after all…
Top 10 Ways to Unblock WEBSITES
How to unblock websites? These days, Internet filtering and controlled access is the new trend. More business owners are implementing filters within their companies with the purpose of blocking websites. Their intention is understandable but, on the other side, people love freedom and sometimes they feel mistreated. However, here are some things you can do that will help you bypass filters and unblock websites.

1. Use web proxies.
Many free online services allow you to access blocked websites through a proxy server. A proxy server is an intermediary between the user and the server where the request was send. Here is a list with the most known resources of web proxies: Proxy.org, HideMyAss.com, Kortaz.com, KProxy.com and Anonymouse.org

1. Use web proxies.
Many free online services allow you to access blocked websites through a proxy server. A proxy server is an intermediary between the user and the server where the request was send. Here is a list with the most known resources of web proxies: Proxy.org, HideMyAss.com, Kortaz.com, KProxy.com and Anonymouse.org
Hidden Commands in XP
1- Private Character Editor
This program is for designing icons and Characters(Alphapet)
Click :start
Then :run
type :EUDCEDIT
..................................................
This program is for designing icons and Characters(Alphapet)
Click :start
Then :run
type :EUDCEDIT
..................................................
NOKIA UNIVERSAL CODES

NOKIA
Nokia Universal Codes
Code Description :
These Nokia codes will work on most Nokia Mobile Phones
Google Hacks Version 1.6
Posted by
STEALTH_HACKER
on Tuesday, July 13, 2010
Labels:
FULL SOFTWARES,
GOOGLE TRICKS n HACKS
/
Comments: (1)
Google Hacks is a compact utility that will allow its users to search google using
different google search hacks. Using Google Hacks one can easily do a music search
by using a highly optimized and complex search command that can be obtained just by
clicking a number of option boxes that can be found in the program´s interface.
Sify Hack For Free Internet !
Use Internet For Free, only sify users
U need are a few utilities like angry ip scanner and a Mac Address changer like Gentle Mac Pro. What you got to do fist is scan your ip range and see who all are online then get their mac address. Then use Gentle Mac Pro and change your ip and mac address to some one who is logged on and Bingo you surfing the net for Free. Here are the Link'z
U need are a few utilities like angry ip scanner and a Mac Address changer like Gentle Mac Pro. What you got to do fist is scan your ip range and see who all are online then get their mac address. Then use Gentle Mac Pro and change your ip and mac address to some one who is logged on and Bingo you surfing the net for Free. Here are the Link'z
Use GMail As An Online Storage System
Use GMail As An Online Storage System This is a fairly simple and useful trick to score yourself a gigabyte's worth of free online file storage.
Hack Remote PC's Using Windows XP as Operating System Using Telnet : Complete Tutorial
Hello Guys I am Going To Explain The Tutorial On Hacking By Using Telnet Service Of Windows Hacking.
NOTE: Will only work if the person you are trying to hack is using a Windows Xp operating system.You need to know victims computers username and password.
Have to be instant messaging victim
Where The Saved Passwords Stores In Windows Xp & Vista - Must for hackers and Beginers
Hello Guys Today i am going to Explain the very basic things that you must know If you Want to become a Hacker or you are a Hacker (whatever be). In this Tutorial I will Explain you "Locations where the passwords are Saved in Windows Operating System". Various readers of my blog asked me about where the passwords really stored in windows. So today I am going to Explain this where the password really stores...So Read on...
This Tutorial is Program Oriented Means Different Locations for Different Softwares and window components...
This Tutorial is Program Oriented Means Different Locations for Different Softwares and window components...
Sponsers
SUBSCRIBE OUR POSTS!
Labels
- AIRTEL TRICKS (2)
- ANTIVIRUS (9)
- BLUETOOTH HACKING (1)
- BOMB TUTORIALS (2)
- COMPUTER TRICKS (44)
- CONTACT ME (1)
- COOL TRICKS (25)
- DATA RECOVERY (5)
- EBOOKS (10)
- EMAIL HACKING (6)
- FACEBOOK HACKING (12)
- FACTS (2)
- FIREFOX TIPS (3)
- FREE GPRS TRICKS (9)
- FULL SOFTWARES (18)
- GAMES HACKING (2)
- GMAIL TIPS n HACKS (8)
- GOOGLE TRICKS n HACKS (15)
- HACK (7)
- HACK IP ADDRESS (7)
- HACKING (8)
- HACKING TOOLS (8)
- HACKING TUTORIALS (22)
- HACKING VIDEOS (2)
- HIDE IP (4)
- HOTMAIL HACKING (1)
- HOW TO (12)
- INTERNET TRICKS (9)
- LEARN HACKING (22)
- MOBILE TRICKS (17)
- MOVIES (37)
- MSN HACKING (3)
- MYSPACE TRICKS n HACKS (7)
- NOTEPAD TRICKS (22)
- OPREATING SYSTEM (5)
- ORKUT TRICKS n HACKS (26)
- PASSWORD HACKING (7)
- PAYPAL HACKING (2)
- PC GAMES (43)
- PHP n MYSQL TUTORIALS (5)
- PREMIUM ACCOUNTS (1)
- RAPIDSHARE HACKS (3)
- RED HAT HACKING (15)
- REGISTRY HACK (1)
- SAFETY TIPS (8)
- SIM CARD CLONING (2)
- TELCOM HACKS (2)
- TIPS n TRICKS (35)
- TUTORIALS (27)
- TWITTER ACCOUNT HACK (4)
- VIRUS CODES (4)
- VIRUS REMOVAL TUTORIAL (5)
- WATCH ONLINE TV (1)
- WEBSITE HACKING (5)
- WINDOWS 7 (8)
- WINDOWS HACKING (4)
- WINDOWS VISTA (7)
- WINDOWS XP TRICKS (39)
- YAHOO TRICKS n HACKS (7)
- YOUTUBE TIPS n HACKS (5)
Blog Archive
-
▼
2010
(598)
-
▼
July
(52)
- Download free Anti-Theft software for your mobile ...
- Start multiple applications with single click : La...
- Add more options to right click in Windows Explorer
- Hiren’s BootCD: What is it??
- How to use Cheat Engine for speedhack in CS 1.6
- How to show a banner at each startup in Windows
- How To Hide Files In A Calculator?
- How to Completely Erase a Hard Disk Drive?
- Display Legal Notice on Startup of your Windows
- What are Private and Public IP Addresses??
- How to Detect Anonymous IP Addresses
- Netbios Hacking- The Ethical Hacking
- What are IP Addresses??
- Shutdown your PC remotely using Twitter and TweetMyPC
- Learn Hacking Step by Step – Understanding the Dan...
- A Port Scanner in VB
- Basic BIOS password crack
- CRACK WIFI – Simple WEP Crack
- How to Shutdown Computer automatically Using Firef...
- Windows 7 God Mode
- 110 Rapidshare premium link generators (unlimited ...
- How do I Check the Real Link of a Shortened URL?
- Exploiting Redirect Vulnerabilities
- 10 Tips to Secure Your Twitter Account
- wαит тσ wяiтє likє тнiร??????????.....
- Top Movies on Computer Hackings
- 221 Microsoft Toggle Keys
- SMS ShortCuts.......!!
- Very useful shopping informat
- Top 10 Ways to Unblock WEBSITES
- Hidden Commands in XP
- NOKIA UNIVERSAL CODES
- some funny cmd hacks
- Windows Hacking Tools
- Google Hacks Version 1.6
- Sify Hack For Free Internet !
- Use GMail As An Online Storage System
- Hack Remote PC's Using Windows XP as Operating Sys...
- Where The Saved Passwords Stores In Windows Xp & V...
- Full Speed Internet Booster 3.3
- CONTACT ME
- speed up your internet
- How to Make Explosive Pen
- How to make Dry Ice Bomb
- Unable To format Your Pendrive ?
- How To delete files in your Inbox
- MANY OF YOU GUYZ ALREADY KNOWING THIS BUT THI...
- How To Play Mobiles Games In Full Screen
- How To Add Windows 7 To XP Boot Screen?
- Tips to Secure and Productive Hacking Email Address
- BEST BATCH TUTORIAL
- HOW TO BLOCK UNWANTED MAILS IN GMAIL YAHOO HOTMAIL..
-
▼
July
(52)
MAP STATS
ONLINE PEOPLES
2009 - STEALTH HACKER is proudly powered by Blogger
Blogger Templates created by Deluxe Templates
Wordpress Web Hosting on Templatelite.com
Blogger Templates created by Deluxe Templates
Wordpress Web Hosting on Templatelite.com




























